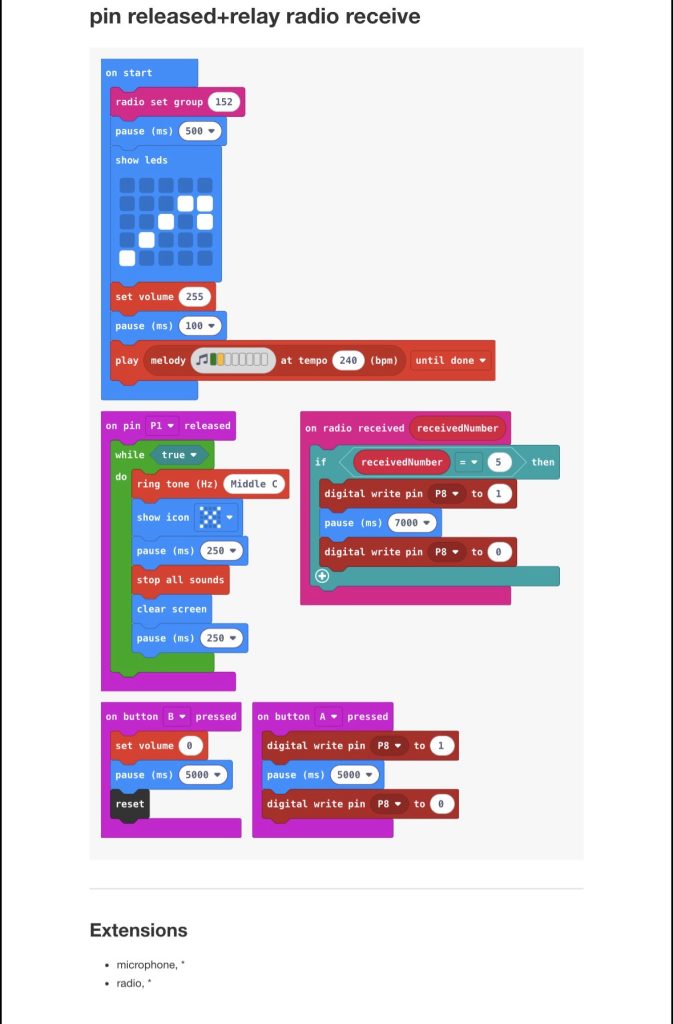
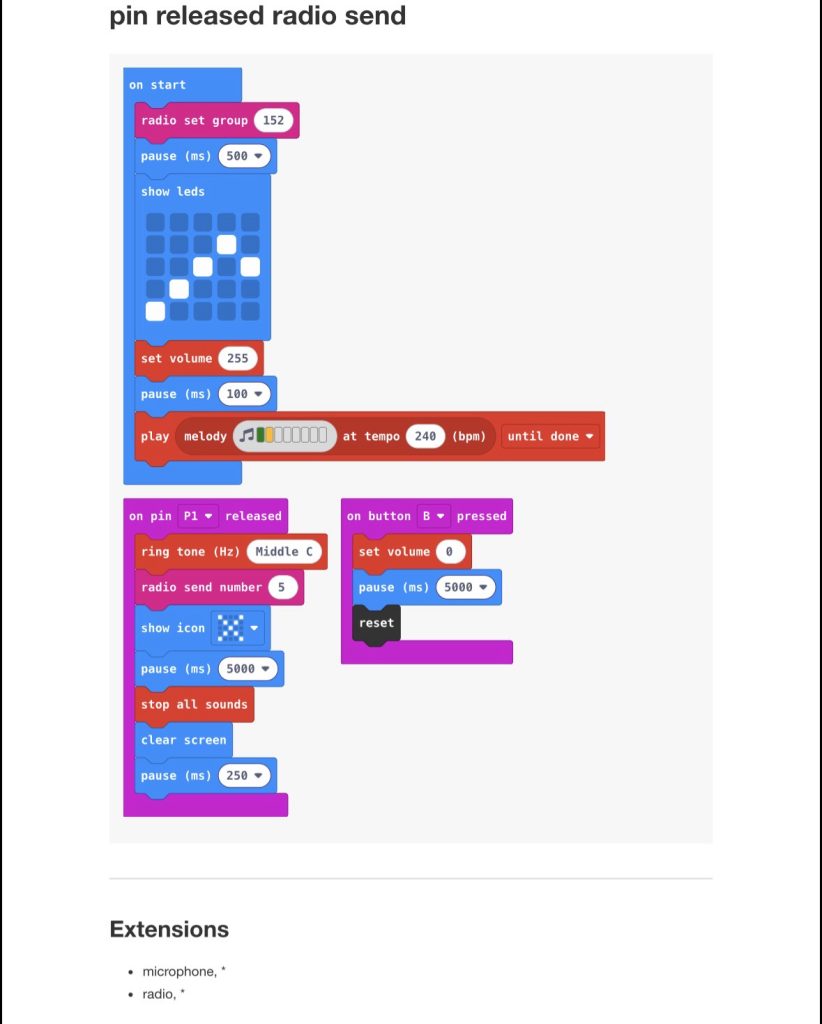
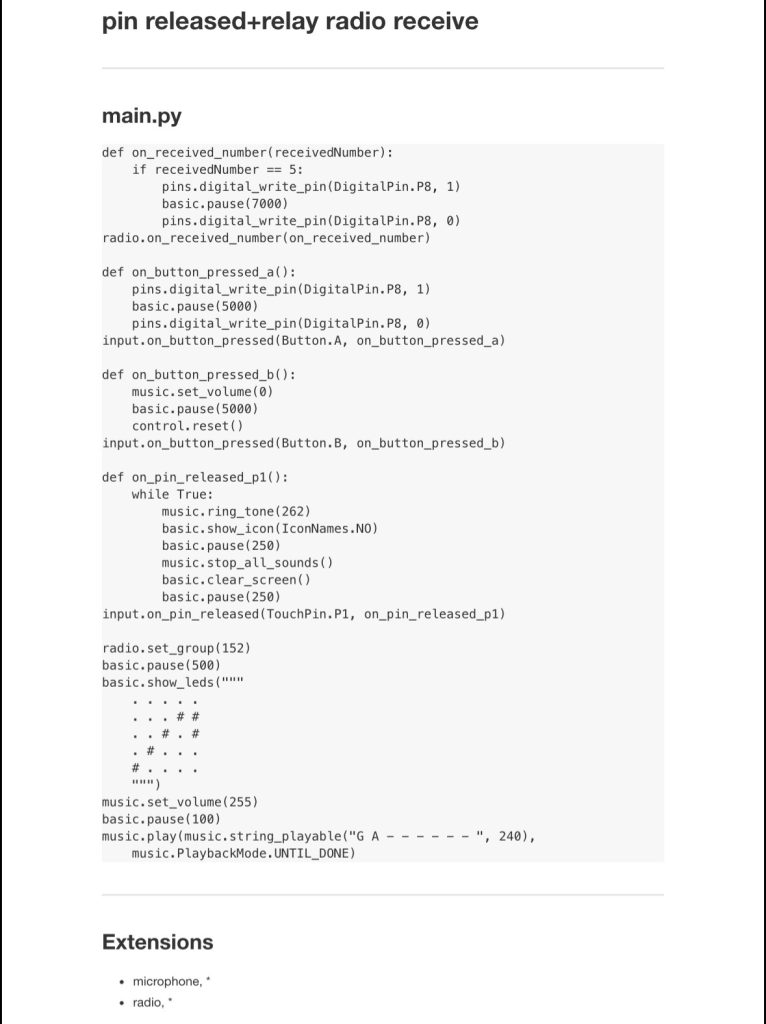
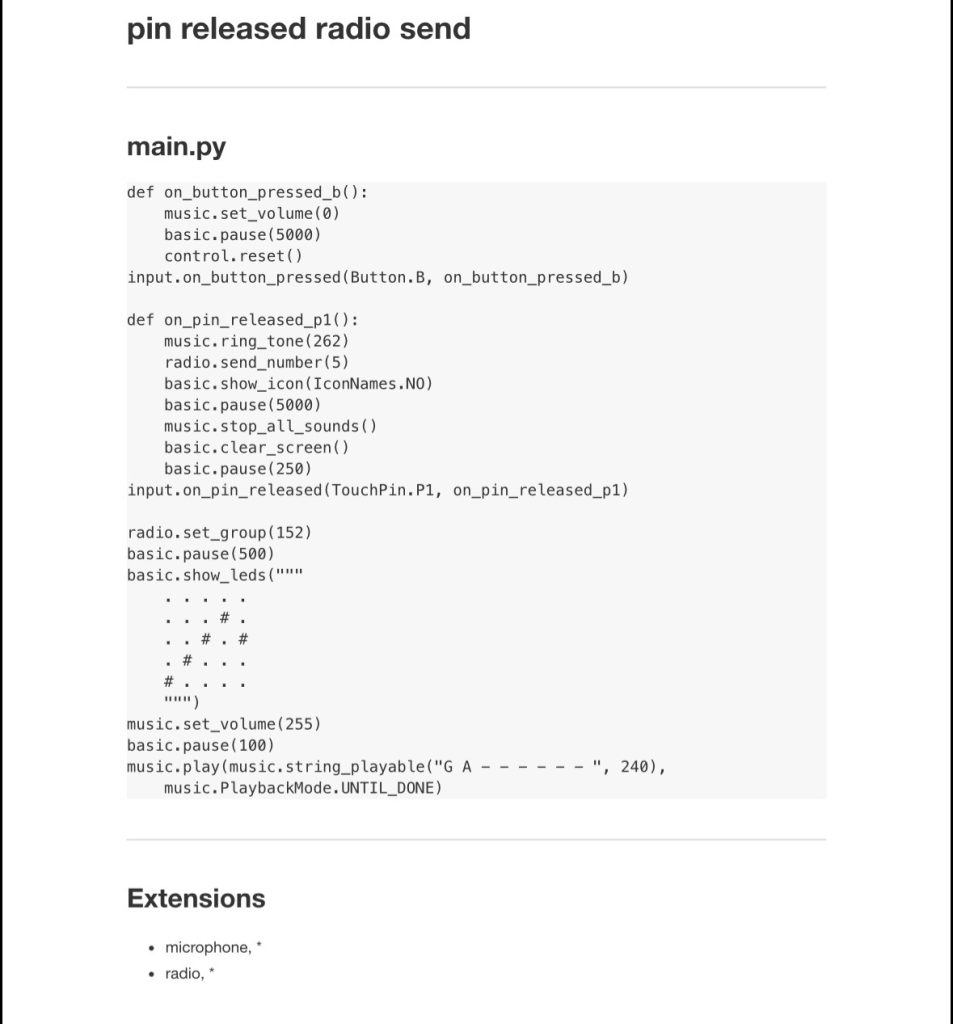
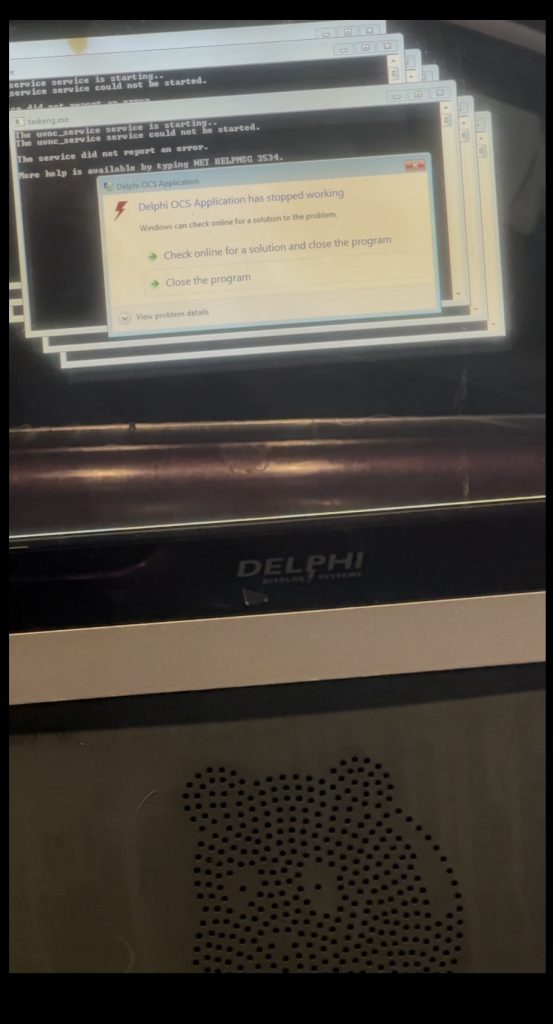
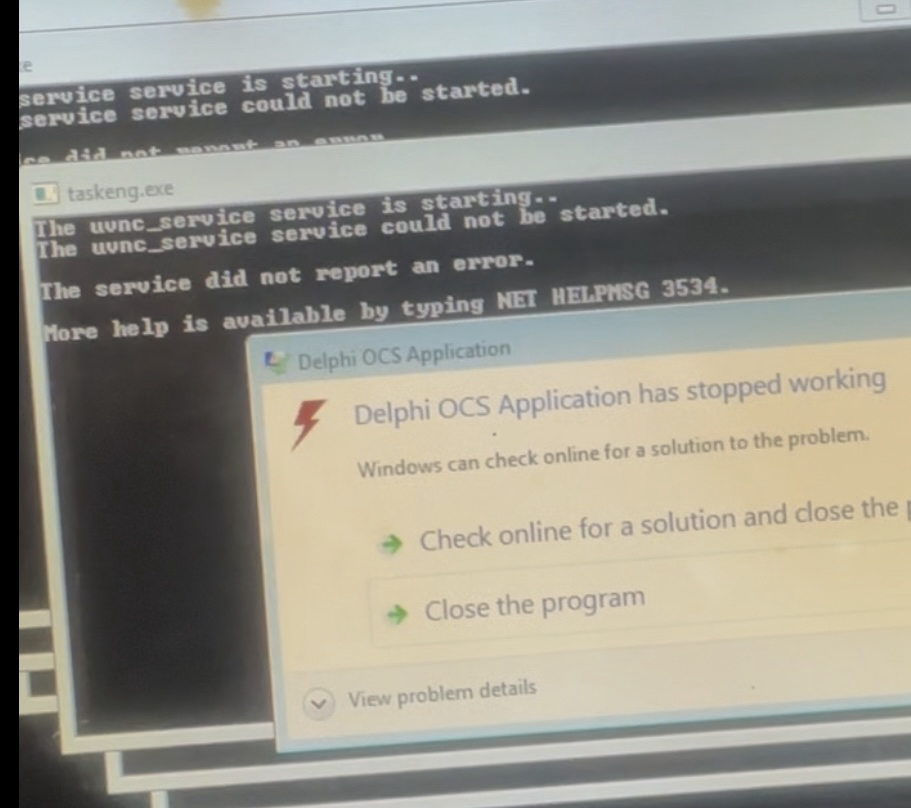
(I recommend 2X speed when watching.) Command execution errors 10 times (red text appear on the big screen after the end of command execution.) on the 11th execution it the reverse shell completes successfully as seen on little Pi’s screen.
#After discovering my split rev shell scheduled task (dirty drive persistance) was getting blocked by Windows Defender, I tried altering the script many times and got inconclusive results, I came to realize it was working properly after executing the script/commands 11 times. At the time of this note I do not know what causes this and the amount of times it must be executed before it’s allowed through the antivirus differs for different computers (i tested my personal hp laptop and my work lenovo laptop. The lenovo seems to only need 3 or 4 executions, sometimes works 1st time). I do not know if it’s an OS, Powershell, or other software version issue.
—got this out of my codex, so this is from a few years ago. I need to revisit the mystery…
—text above that starts with a hashtag is from my codex notes.
In the video:
—The little screen is the raspberry pi listening for an inbound connection with ncat. (It’s a reverse shell scenario)
—On the computer using Windows and powershell, the commands for a reverse shell are being injected with a HID keyboard injector and is coded to repeat the same set of actions so I didn’t have to do it manually.